I recently saw Linus Neumann from the Chaos Computer Club in a video talking about IT security myths which I try to explain all time, however Linus listed them so elegantly in his video, I want to repeat them as text:
❔ "Why should they be interested in me?"
Answer: Their business model is not based on customers. The attackers are not interested in you. They just cast their net and you just got/will get caught as one of many fish. They go for the masses in which you are part of, not you as a person.❔ "My password is very strong, so I use it everywhere!"
Answer: You password must be unique per site/service! If one site is hacked, you might not even know about it and your credentials can be used everywhere, because they are not unique. Follow the tipps here.❔ "The attackers want to hurt me!"
Answer: No, mostly they just want to make money. In a ransomware attack for example they dont want to hurt you. Instead they want to get your money.❔ "This is now secure and it stays that way."
Answer: IT-Security is an onging process. IT systems have an operating system, applications, libraries, middleware etc which all consist of many million lines of software code. And in these lines of code are many vulnerabilites, which are not found yet. But some day they will be found, get public knowledge and can be exploited. That is why IT security is an onging process.❔ "Attackers have special technical skills."
Answer: Some might, but often they dont. Because when a vulnerability becomes public knowledge most of the time an exploit is written. And that exploit can be used by anyone. That is why its "not fair" - the attackes have and this as an advantage.❔ "Everything can be hacked, so we are powerless!"
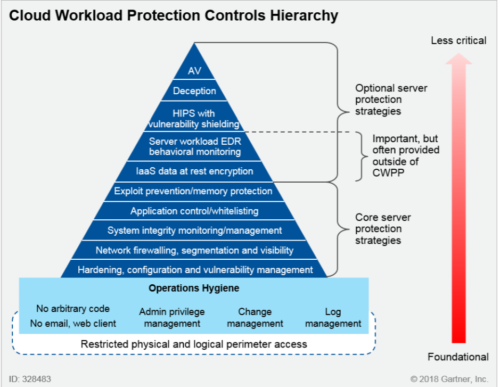
Answer: No, because there are many things which can be implemented and done, so an attack becomes so hard, that almost no one will try it.Examples can be found here and here or as shown in the graphic: Start with implementing vulnerability-management, hardening (use a framework like cis, nist, etc), implement zero trust network or microsegmentation, implement 2fa or mfa, etc.
No comments:
Post a Comment