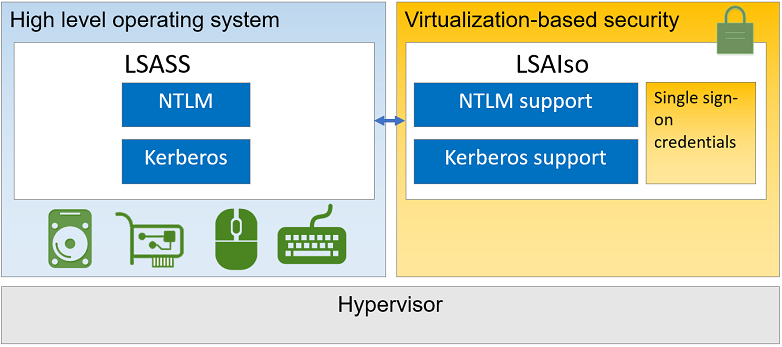
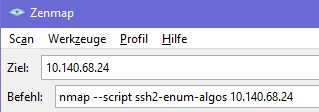
In case of an IT-security incident, emergency oder if a new critical vulnerability (like log4j in December 2021) arises, it is good to be prepared, so you can quickly answer questions like:
- "Are we affected?"
- "Do we use this technology?"
- "Where do we use this vulnerable protocol?"
- "To whom is the attack surface exposed to?"
- "Are there mitigations in place?"
- "Is is exploitable without authentication in our setup?"
- "Which is the best place to place a first mitigation?"
- etc..
| System | Internet Facing | Protocol | Authentication | Security | Used Products/Vendors | Logs send to SIEM | Contact Person | Known Weaknesses |
| Websites | Yes, exposed to all public-ip-addresses | HTTPS (TCP:443) & HTTP (TCP:80 - HTTP 301 Redirect to HTTPS) | None | Web Application Firewall | F5 BigIP LoadBalancer WAF & Apache Container on OpenShift | Yes | Link to CMDB | Websites may contain 3rd party code, SBOM see CMDB |
| Managed File Transfer | Yes, but limited to dedicated public ip-addresses of partners | HTTPS (TCP:443) | HTTPS Tokens | Web Application Firewall | F5 BigIP LoadBalancer WAF IPSwitch | Yes | Link to CMDB | Runs on VM as appliance, OS might not be hardend from vendor |
| Citrix | Yes, exposed to all public-ip-addresses | HTTPS (TCP:443) | MFA | Netscaler WAF | Citrix Systems + Okta MFA | Yes | Link to CMDB | NetScaler WAF Ruleset might be out-of-date |
| Mailserver | Yes, exposed to all public-ip-addresses | SMTP (TCP:25) | None | AntiSpam Mailgatway & AV-Sandbox | Cisco E-Mail Security | Yes | Link to CMDB | Mailgateways run on Hardware, might not be hardended from vendor |
| SSLVPN S2E | Yes, exposed to all public-ip-addresses | HTTPS (TCP:443) | Mutual TLS Certbased + MFA | Azure DDoS | FortiGate SSLVPN Azure VM + Okta MFA | Yes | Link to CMDB | Possible FortiGate FortiOS SSLVPN Vulnerabilities |
| M365 ActiveSync | Yes, exposed to all public-ip-addresses | HTTPS (TCP:443) | Mutual TLS Certbased | Azure DDoS | Microsoft 365 + Intunes | Yes | Link to CMDB | Not part of own Vulnerability-Scanner |
| VPN S2S | Yes, but limited to dedicated public ip-addresses of partners | IPSec UDP:500 & UDP:4500 & ESP | IPsec IKEv2 Certbased Auth | Azure DDoS | FortiGate SSLVPN Azure VM | Link to CMDB | - | |
| DMARC SaaS | Yes, exposed to all public-ip-addresses | DNS (UDP:53), HTTP (TCP:80), HTTPS (TCP:443), SMTP (TCP:25) | None | - | dmarcadvisor.com SaaS | No | Link to CMDB | Not part of own Vulnerability-Scanner |
| DNS Server | Yes, but limited to dedicated public ip-addresses of partners | DNS (UDP:53 & TCP:53) | None | Azure Network Security Groups | RHEL Bind | Yes | Link to CMDB | - |
| ISP Routers | Yes, but limited to dedicated public ip-addresses of ISP routers | BGP (TCP:179), BFD, Ping (ICMP:0/8) | BGP MD5 Auth | - | Extreme Networks XOS | Yes | Link to CMDB | |
| etc.. | etc.. | etc.. | etc.. | etc.. | etc.. | etc.. | etc.. | etc.. |
Of course you can add many more columns like e.g.:
- "SBOM technologys used" (for example: RHEL, Apache Tomcat, OpenSSL, log4j, puppet, ansible, splunk universal forwarder, appdynamics,..)
- Direct links to your Firewall Management System, WAF or SIEM
- "Is it part of our vulnerability scanner?"
- "Is the vulnerability scanner scanning it authenticated?"
- "Is the system/application hardended?"
- and so on :-)