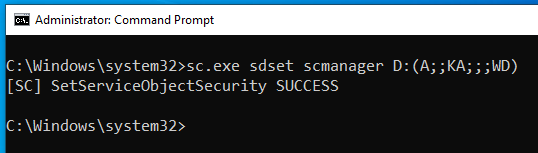
Alh4zr3d and Grzegorz Tworek wrote about a fileless, local privilege escalation backdoor in order to gain persistence (TA0003) using the following Windows command:
sc.exe sdset scmanager D:(A;;KA;;;WD)
Setting the security descriptor on the service manager allows anyone to start SYSTEM services.
To show the security descriptor of service manager:
sc.exe sdshow scmanager
The Mitre Att&ck framework has technique T1569.002 for this "System Services: Service Execution", writing: "Adversaries may abuse the Windows service control manager to execute
malicious commands or payloads. The Windows service control manager (services.exe) is an interface to manage and manipulate services. The service control manager is accessible to users via GUI components as well as system utilities such as sc.exe and Net."
Microsofts own documentation about sc.exe sdset:
Sets a service's security descriptor, using the Service Descriptor Definition Language (SDDL).
Syntax
sc [<ServerName>] sdset <ServiceName> <ServiceSecurityDescriptor>Parameters
Parameter
Description
<ServerName>
Specifies the name of the remote server on which the service is located. The name must use the Universal Naming Convention (UNC) format (for example, \\myserver). To run SC.exe locally, omit this parameter.
<ServiceName>
Specifies the service name returned by the getkeyname operation.
<ServiceSecurityDescriptor>
Specifies the service descriptor in SDDL.
/?
Displays help at the command prompt.
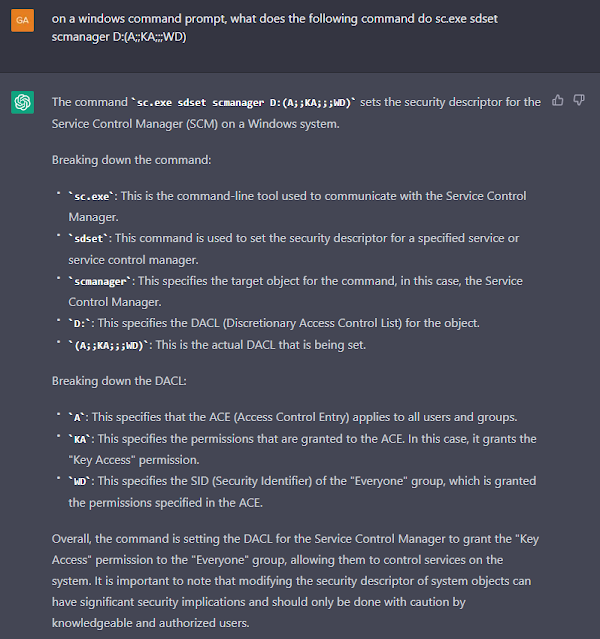
To explain the DACL D:(A;;KA;;;WD) gav_gall asked ChatGPT to explain: