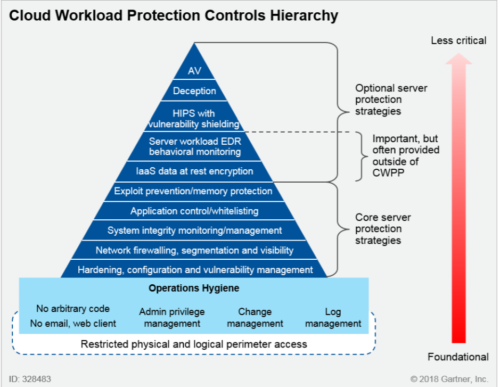
A few basic tasks in Microsoft Azure via CLI. In order to use microsegmentation or zero-trust-networking in Azure (which I highly recommend), I recommend to work with Azure Network Security Groups.
List Azure VM ip-addresses
Azure:~$
Azure:~$ az vm list-ip-addresses
[
{
"virtualMachine": {
"name": "my-vm",
"network": {
"privateIpAddresses": [
"10.0.0.4"
],
"publicIpAddresses": [
{
"id": "/subscriptions/9aaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa7/resourceGroups/learn-f00f00f0-f00f-f00f-f00f-f00f00f00f00
"ipAddress": "13.64.0.1",
"ipAllocationMethod": "Dynamic",
"name": "my-vmPublicIP",
"resourceGroup": "learn-f00f00f0-f00f-f00f-f00f-f00f00f00f00"
}
]
},
"resourceGroup": "learn-f00f00f0-f00f-f00f-f00f-f00f00f00f01"
}
}
]
Azure:~$
Azure:~$
Put IP-address of VM in variable
IPADDRESS="$(az vm list-ip-addresses \
--resource-group learn-f00f00f0-f00f-f00f-f00f-f00f00f00f00 \
--name my-vm \
--query "[].virtualMachine.network.publicIpAddresses[*].ipAddress" \
--output tsv)"
Azure:~$
Azure:~$ IPADDRESS="$(az vm list-ip-addresses \
> --resource-group learn-f00f00f0-f00f-f00f-f00f-f00f00f00f00 \
> --name my-vm \
> --query "[].virtualMachine.network.publicIpAddresses[*].ipAddress" \
> --output tsv)"
Azure:~$
Azure:~$
Azure:~$ echo $IPADDRESS
13.64.0.1
Azure:~$
Azure:~$
Azure:~$ curl --connect-timeout 5 http://$IPADDRESS
curl: (28) Connection timed out after 5000 milliseconds
Show Azure Network Security Group
Azure:~$
Azure:~$ az network nsg list \
> --resource-group learn-f00f00f0-f00f-f00f-f00f-f00f00f00f00 \
> --query '[].name' \
> --output tsv
my-vmNSG
Azure:~$
Azure:~$
Azure Network Security Group Name = my-vmNSG
What is defined in Network Security Group Name my-vmNSG?
Azure:~$
Azure:~$
Azure:~$ az network nsg rule list \
> --resource-group learn-f00f00f0-f00f-f00f-f00f-f00f00f00f00 \
> --nsg-name my-vmNSG
[
{
"access": "Allow",
"description": null,
"destinationAddressPrefix": "*",
"destinationAddressPrefixes": [],
"destinationApplicationSecurityGroups": null,
"destinationPortRange": "22",
"destinationPortRanges": [],
"direction": "Inbound",
"etag": "W/\"ae2ae2ae-ae2a-ae2a-ae2a-ae2aae2aae2a
"id": "/subscriptions/9aaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa7/resourceGroups/learn-f00f00f0-f00f-f00f-f00f-f00f00f00f00
"name": "default-allow-ssh",
"priority": 1000,
"protocol": "Tcp",
"provisioningState": "Succeeded",
"resourceGroup": "learn-f00f00f0-f00f-f00f-f00f-f00f00f00f01
"sourceAddressPrefix": "*",
"sourceAddressPrefixes": [],
"sourceApplicationSecurityGroups": null,
"sourcePortRange": "*",
"sourcePortRanges": [],
"type": "Microsoft.Network/networkSecurityGroups/securityRules"
}
]
Azure:~$
Azure:~$
Show again that JSON formated by Name, Prio, Dst-Port & Access-Action:
Azure:~$
Azure:~$ az network nsg rule list \
> --resource-group learn-f00f00f0-f00f-f00f-f00f-f00f00f00f01
> --nsg-name my-vmNSG \
> --query '[].{Name:name, Priority:priority, Port:destinationPortRange, Access:access}' \
> --output table
Name Priority Port Access
----------------- ---------- ------ --------
default-allow-ssh 1000 22 Allow
Azure:~$
Azure:~$
Create Azure Network Security Group Rule for HTTP
Azure:~$
Azure:~$ az network nsg rule create \
> --resource-group learn-f00f00f0-f00f-f00f-f00f-f00f00f00f01
> --nsg-name my-vmNSG \
> --name allow-http \
> --protocol tcp \
> --priority 100 \
> --destination-port-range 80 \
> --access Allow
{- Finished ..
"access": "Allow",
"description": null,
"destinationAddressPrefix": "*",
"destinationAddressPrefixes": [],
"destinationApplicationSecurityGroups": null,
"destinationPortRange": "80",
"destinationPortRanges": [],
"direction": "Inbound",
"etag": "W/\"ae2ae2ae-ae2a-ae2a-ae2a-ae2aae2aae2a
"id": "/subscriptions/9aaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa7learn-f00f00f0-f00f-f00f-f00f-f00f00f00f01
"name": "allow-http",
"priority": 100,
"protocol": "Tcp",
"provisioningState": "Succeeded",
"resourceGroup": "learn-f00f00f0-f00f-f00f-f00f-f00f00f00f01
"sourceAddressPrefix": "*",
"sourceAddressPrefixes": [],
"sourceApplicationSecurityGroups": null,
"sourcePortRange": "*",
"sourcePortRanges": [],
"type": "Microsoft.Network/networkSecurityGroups/securityRules"
}
Azure:~$
Azure:~$
Show that in JSON:
Azure:~$
Azure:~$ az network nsg rule list \
> --resource-group learn-f00f00f0-f00f-f00f-f00f-f00f00f00f01
> --nsg-name my-vmNSG
[
{
"access": "Allow",
"description": null,
"destinationAddressPrefix": "*",
"destinationAddressPrefixes": [],
"destinationApplicationSecurityGroups": null,
"destinationPortRange": "22",
"destinationPortRanges": [],
"direction": "Inbound",
"etag": "W/\"ae2ae2ae-ae2a-ae2a-ae2a-ae2aae2aae2a
"id": "/subscriptions/9aaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa7learn-f00f00f0-f00f-f00f-f00f-f00f00f00f01
"name": "default-allow-ssh",
"priority": 1000,
"protocol": "Tcp",
"provisioningState": "Succeeded",
"resourceGroup": "learn-f00f00f0-f00f-f00f-f00f-f00f00f00f01
"sourceAddressPrefix": "*",
"sourceAddressPrefixes": [],
"sourceApplicationSecurityGroups": null,
"sourcePortRange": "*",
"sourcePortRanges": [],
"type": "Microsoft.Network/networkSecurityGroups/securityRules"
},
{
"access": "Allow",
"description": null,
"destinationAddressPrefix": "*",
"destinationAddressPrefixes": [],
"destinationApplicationSecurityGroups": null,
"destinationPortRange": "80",
"destinationPortRanges": [],
"direction": "Inbound",
"etag": "W/\"ae2ae2ae-ae2a-ae2a-ae2a-ae2aae2aae2a
"id": "/subscriptions/9aaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa7learn-f00f00f0-f00f-f00f-f00f-f00f00f00f01
"name": "allow-http",
"priority": 100,
"protocol": "Tcp",
"provisioningState": "Succeeded",
"resourceGroup": "learn-f00f00f0-f00f-f00f-f00f-f00f00f00f01
"sourceAddressPrefix": "*",
"sourceAddressPrefixes": [],
"sourceApplicationSecurityGroups": null,
"sourcePortRange": "*",
"sourcePortRanges": [],
"type": "Microsoft.Network/networkSecurityGroups/securityRules"
}
]
Azure:~$
Azure:~$
Azure:~$ az network nsg rule list \
> --resource-group learn-f00f00f0-f00f-f00f-f00f-f00f00f00f01
> --nsg-name my-vmNSG \
> --query '[].{Name:name, Priority:priority, Port:destinationPortRange, Access:access}' \
> --output table
Name Priority Port Access
----------------- ---------- ------ --------
default-allow-ssh 1000 22 Allow
allow-http 100 80 Allow
Azure:~$
Azure:~$