Microsoft Threat Protection Intelligence Team released in the past some great detailed articles (e.g. 2020-03 Ransomware, 2018-03 FinFisher, 2017-05 wannacry, 2017-06 petya) about different real world attack chains including a mapping to MITREs framework Att&ck.
Parinacota attack chain

The
article on Parinacota includes details like how for example persistence is archived:
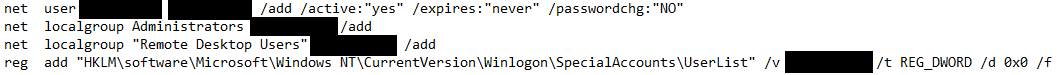
- Windows Registry modifications using .bat or .reg files to allow RDP connections

- Setting up access through existing remote assistance apps or installing a backdoor
- Creating new local accounts and adding them to the local administrators group
Wadhrama attack chain
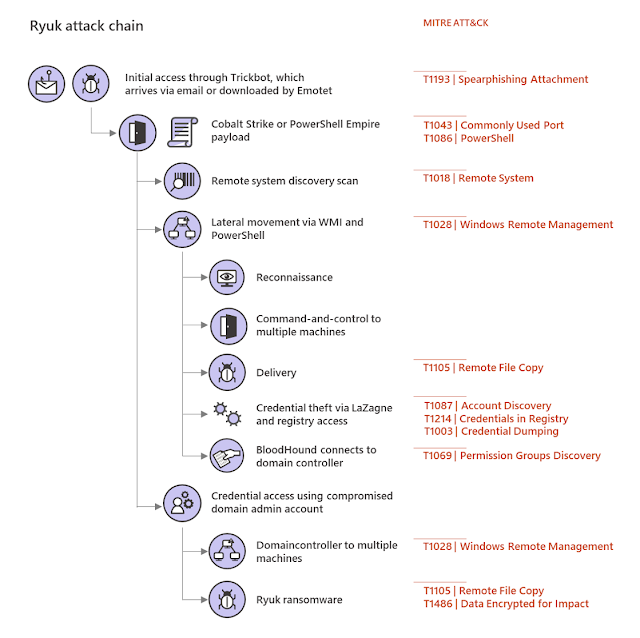
Ryuk attack chain
Doppelpaymer attack chain






No comments:
Post a Comment