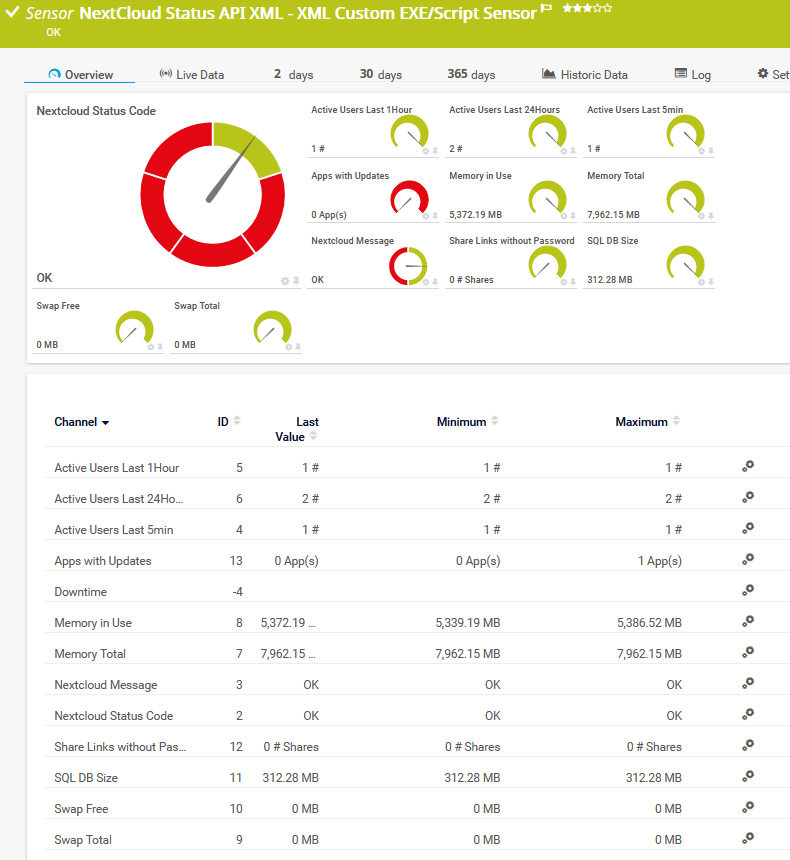
In order to monitor your Nextcloud API (XML) via PRTG, you can use the following steps:
https://github.com/flostyen/PRTGScripts/tree/master/PRTG-NextCloud-Status which is a fork of https://github.com/freaky-media/PRTGScripts/blob/master/PRTG-NextCloud-Status/ (I simply added TLSv1.2 support and adjusted the howto guide, all the work was done from freaky-media 😊)
1. Installation in PRTG
1.1 Copy the PS1 File to your PRTG server in the path C:\Program Files (x86)\PRTG Network Monitor\Custom Sensors\EXEXML.
If you want to monitoring nextcloud systems from your PRTG remote probes, copy the script to the remote probe.
1.2 Create the following lookup files NextCloudMessageLookup.ovl, NextCloudStatusCodeLookup.ovl, NextCloudStatusLookup.ovl
into your PRTG installation folder C:\Program Files (x86)\PRTG Network Monitor\lookups\custom
1.3 Reload Lookups:
PRTG GUI -> Setup -> System Administration -> Administrative Tools -> Load Lookups and File Lists -> Go! Button
2. Configuration in PRTG
2.1 Add the sensor "EXE/Script Advanced" 
2.2 Change the sensor name
2.3 Choose in the powershell script PRTG_NextCloud.ps1.
2.4 Add parameter
-NCusername *AnExtraNCAdminUser* -NCpassword *StrongPassSentence* -NCURL *YourNCFQDN*





thx a lot. works great. two things to add:
ReplyDeletea) Don't use your admin password/pass-sentence. You must use 2FA with Nextcloud :). Never ever give your admin password to someone. Instead create a devicespecific password for your admin user (https://docs.nextcloud.com/server/20/user_manual/en/session_management.html#device-specific-passwords-and-password-changes).
b) If you run a ps1 file in PRTG for the first time: Change ExecutionPolicy in 32bit powershell to: Set-ExecutionPolicy RemoteSigned and unblock your downloaded file: Unblock-File .\PRTG_NextCloud.ps1
Thank you for your feedback :-) Great that it works for you!
Deletea) You are totally correct, my initial text was not clear enough: Create an extra account for prtg in nextcloud, never use your admin-account.
b) You dont have to change the powershell executionpolicy (possible security risk*), simply unblocking the ps script is enough, as stated in microsoft docs https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.utility/unblock-file?view=powershell-7.1 „The Unblock-File cmdlet lets you open files that were downloaded from the Internet. It unblocks PowerShell script files that were downloaded from the Internet so you can run them, even when the PowerShell execution policy is RemoteSigned. By default, these files are blocked to protect the computer from untrusted files.“
* = depending on your prtg system exposure, hardening, patchlevel, etc. It also matters if your are using Windows Client OS or Windows Server OS due to microsofts powershell executionpolicy default: „Default - Sets the default execution policy. Restricted for Windows clients or RemoteSigned for Windows servers.“ (https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.security/set-executionpolicy?view=powershell-7.1)
Very nice information I like your style.....PRTG Network Monitor
ReplyDeleteBuenas tardes, a mi me da este error!
ReplyDeleteAPI Query Failed: The underlying connection was closed: Could not establish trust relationship for the SSL/TLS secure channel.
Y no le encuentro la solucion