When you suspect your Microsoft Defender Antivirus to be a bottleneck for your Windows performance, then you may use Microsofts Defender Antivirus performance analyzer. It helps you with the on-premise Windows Defender Antivirus as well as with the cloud solution Microsoft Defender for Endpoint (Defender ATP).
Especially on developer systems with an IDE Microsoft Defender Antivirus can have a significant performance impact on your system due to the many temporary files, which are not digitally signed but contain exectuable code. Microsofts Defender Antivirus performance can help you to detect:
- Files with long antivirus scan times
- Processes with long antivirus scan times
- File extensions with long antivirus scan times
Running defender antivirus performance analyzer
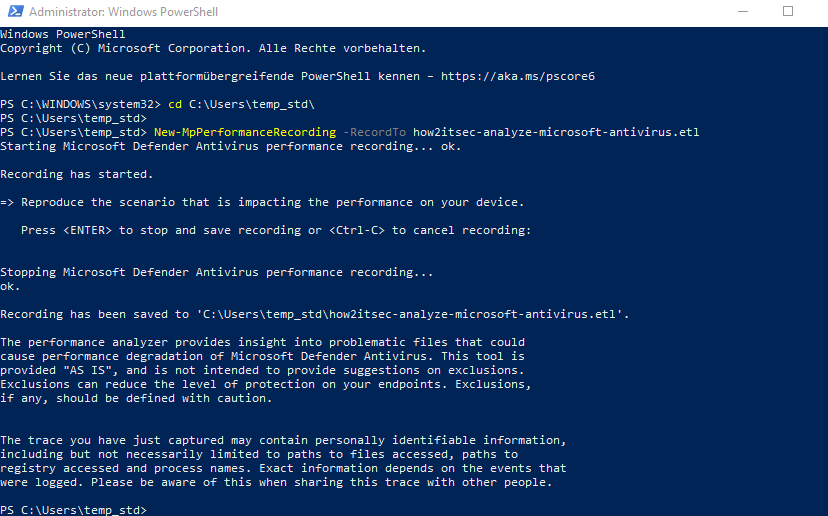
- Run PowerShell (Admin)
- Use the PowerShell command
New-MpPerformanceRecording -RecordTo how2itsec-analyze-microsoft-antivirus.etl - Repeate your performance issue, e.g. building your software or opening a programm
- Press Enter to stop the trace
Analysis of the trace
Get-MpPerformanceReport [-Path] <String>
[-TopScans <Int32>]
[-TopFiles <Int32>
[-TopScansPerFile <Int32>]
[-TopProcessesPerFile <Int32>
[-TopScansPerProcessPerFile <Int32>]
]
]
[-TopExtensions <Int32>
[-TopScansPerExtension <Int32>]
[-TopProcessesPerExtension <Int32>
[-TopScansPerProcessPerExtension <Int32>]
]
[-TopFilesPerExtension <Int32>
[-TopScansPerFilePerExtension <Int32>]
]
]
]
[-TopProcesses <Int32>
[-TopScansPerProcess <Int32>]
[-TopExtensionsPerProcess <Int32>
[-TopScansPerExtensionPerProcess <Int32>]
]
]
[-TopFilesPerProcess <Int32>
[-TopScansPerFilePerProcess <Int32>]
]
[-MinDuration <String>]
[-Raw]Example Analysis
Get-MpPerformanceReport -Path .\how2itsec-analyze-microsoft-antivirus.etl -TopFiles 10
Get-MpPerformanceReport -Path .\how2itsec-analyze-microsoft-antivirus.etl -TopFiles 10 -TopScansPerFile 3 
Get-MpPerformanceReport -Path .\how2itsec-analyze-microsoft-antivirus.etl -TopExtensions:10 -TopProcesses:10 -TopScans:10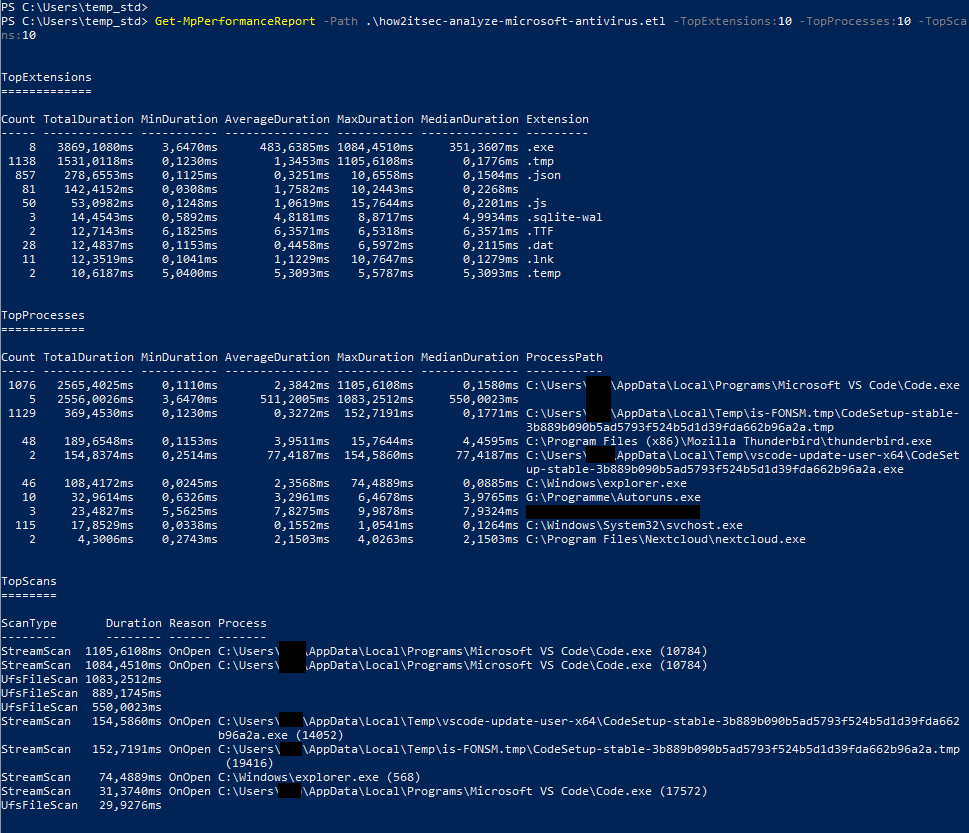
Get-MpPerformanceReport -Path .\how2itsec-analyze-microsoft-antivirus.etl -TopScans:100 -MinDuration:100ms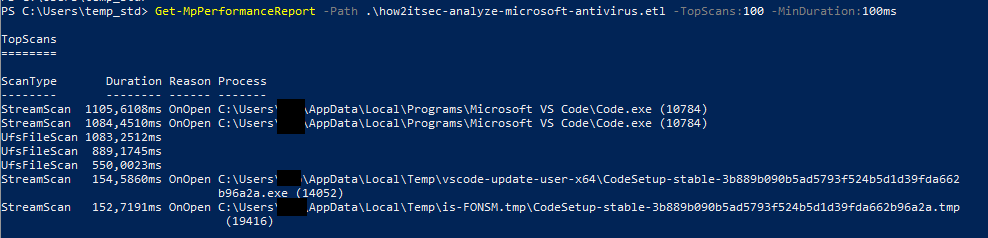
Get-MpPerformanceReport -Path .\how2itsec-analyze-microsoft-antivirus.etl -TopScans:100 -MinDuration:500ms -Raw | ConvertTo-Js



No comments:
Post a Comment